Download CompTIA DataSys plus.DS0-001.VCEplus.2024-02-12.50q.vcex
| Vendor: | CompTIA |
| Exam Code: | DS0-001 |
| Exam Name: | CompTIA DataSys plus |
| Date: | Feb 12, 2024 |
| File Size: | 1 MB |
| Downloads: | 5 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which of the following is a characteristic of all non-relational databases?
- Columns with the same data type
- Unstructured data
- Logical record groupings
- Tabular schema
Correct answer: B
Explanation:
The characteristic of all non-relational databases is unstructured data. Unstructured data is data that does not have a predefined or fixed format, schema, or structure. Unstructured data can include various types of data, such as text, images, audio, video, etc. Non-relational databases, also known as NoSQL databases, are databases that store and manage unstructured data using different models, such as key-value, document, graph, columnar, etc. Non-relational databases are suitable for handling large volumes, variety, and velocity of data that do not fit well in the relational model. The other options are either characteristics of relational databases or not related to database types at all. For example, columns with the same data type, logical record groupings, and tabular schema are characteristics of relational databases, which are databases that store and manage structured data using tables, rows, columns, and constraints.Reference:CompTIA DataSys+ Course Outline, Domain 1.0 Database Fundamentals, Objective 1.1 Given a scenario, identify common database types. The characteristic of all non-relational databases is unstructured data. Unstructured data is data that does not have a predefined or fixed format, schema, or structure. Unstructured data can include various types of data, such as text, images, audio, video, etc. Non-relational databases, also known as NoSQL databases, are databases that store and manage unstructured data using different models, such as key-value, document, graph, columnar, etc. Non-relational databases are suitable for handling large volumes, variety, and velocity of data that do not fit well in the relational model. The other options are either characteristics of relational databases or not related to database types at all. For example, columns with the same data type, logical record groupings, and tabular schema are characteristics of relational databases, which are databases that store and manage structured data using tables, rows, columns, and constraints.
Reference:
CompTIA DataSys+ Course Outline, Domain 1.0 Database Fundamentals, Objective 1.1 Given a scenario, identify common database types.
Question 2
Which of the following is used to hide data in a database so the data can only be read by a user who has a key?
- Data security
- Data masking
- Data protection
- Data encryption
Correct answer: D
Explanation:
The option that is used to hide data in a database so the data can only be read by a user who has a key is data encryption. Data encryption is a process that transforms data into an unreadable or scrambled form using an algorithm and a key. Data encryption helps protect data from unauthorized access or modification by third parties, such as hackers, eavesdroppers, or interceptors. Data encryption also helps verify the identity and authenticity of the source and destination of the data using digital signatures or certificates. Data encryption can be applied to data at rest (stored in a database) or data in transit (transmitted over a network). To read encrypted data, a user needs to have the corresponding key to decrypt or restore the data to its original form. The other options are either different concepts or not related to hiding data at all.For example, data security is a broad term that encompasses various methods and techniques to protect data from threats or risks; data masking is a technique that replaces sensitive data with fictitious but realistic data to protect its confidentiality or compliance; data protection is a term that refers to the legal or ethical obligations to safeguard personal or sensitive data from misuse or harm.Reference:CompTIA DataSys+ Course Outline, Domain 4.0 Data and Database Security, Objective 4.2 Given a scenario, implement security controls for databases. The option that is used to hide data in a database so the data can only be read by a user who has a key is data encryption. Data encryption is a process that transforms data into an unreadable or scrambled form using an algorithm and a key. Data encryption helps protect data from unauthorized access or modification by third parties, such as hackers, eavesdroppers, or interceptors. Data encryption also helps verify the identity and authenticity of the source and destination of the data using digital signatures or certificates. Data encryption can be applied to data at rest (stored in a database) or data in transit (transmitted over a network). To read encrypted data, a user needs to have the corresponding key to decrypt or restore the data to its original form. The other options are either different concepts or not related to hiding data at all.
For example, data security is a broad term that encompasses various methods and techniques to protect data from threats or risks; data masking is a technique that replaces sensitive data with fictitious but realistic data to protect its confidentiality or compliance; data protection is a term that refers to the legal or ethical obligations to safeguard personal or sensitive data from misuse or harm.
Reference:
CompTIA DataSys+ Course Outline, Domain 4.0 Data and Database Security, Objective 4.2 Given a scenario, implement security controls for databases.
Question 3
A server administrator wants to analyze a database server's disk throughput. Which of the following should the administrator measure?
- RPfvl
- Latency
- IOPS
- Reads
Correct answer: C
Explanation:
The factor that the administrator should measure to analyze a database server's disk throughput is IOPS. IOPS, or Input/Output Operations Per Second, is a metric that measures the number of read and write operations that a disk can perform in one second. IOPS indicates the performance or speed of a disk and how well it can handle multiple requests or transactions. Higher IOPS means higher disk throughput and lower latency. IOPS can be affected by various factors, such as disk type, size, speed, cache, RAID level, etc. The other options are either not related or not sufficient for this purpose. For example, RPfvl is not a valid acronym or metric; latency is the time delay between a request and a response; reads are the number of read operations performed by a disk.Reference:CompTIA DataSys+ Course Outline, Domain 3.0 Database Management and Maintenance, Objective 3.2 Given a scenario, monitor database performance. The factor that the administrator should measure to analyze a database server's disk throughput is IOPS. IOPS, or Input/Output Operations Per Second, is a metric that measures the number of read and write operations that a disk can perform in one second. IOPS indicates the performance or speed of a disk and how well it can handle multiple requests or transactions. Higher IOPS means higher disk throughput and lower latency. IOPS can be affected by various factors, such as disk type, size, speed, cache, RAID level, etc. The other options are either not related or not sufficient for this purpose. For example, RPfvl is not a valid acronym or metric; latency is the time delay between a request and a response; reads are the number of read operations performed by a disk.
Reference:
CompTIA DataSys+ Course Outline, Domain 3.0 Database Management and Maintenance, Objective 3.2 Given a scenario, monitor database performance.
Question 4
Which of the following have data manipulation and procedural scripting power? (Choose two.)
- PQL
- PL/SQL
- Advanced
- SQL
- SQL
- T-SQL
Correct answer: BF
Explanation:
The two options that have data manipulation and procedural scripting power are PL/SQL and T-SQL. PL/SQL, or Procedural Language/Structured Query Language, is an extension of SQL that adds procedural features to SQL for Oracle databases. PL/SQL allows users to create and execute stored procedures, functions, triggers, packages, etc., using variables, loops, conditions, exceptions, etc., in addition to SQL commands. PL/SQL helps improve the performance, functionality, modularity, and security of SQL queries and applications. T-SQL, or Transact-SQL, is an extension of SQL that adds procedural features to SQL for Microsoft SQL Server databases. T-SQL allows users to create and execute stored procedures, functions, triggers, etc., using variables, loops, conditions, exceptions, etc., in addition to SQL commands. T-SQL helps improve the performance, functionality, modularity, and security of SQL queries and applications. The other options are either not related or not having both data manipulation and procedural scripting power. For example, PQL, or Power Query Language, is a data analysis and transformation language for Microsoft Power BI and Excel; Advanced SQL is a term that refers to the advanced features or techniques of SQL, such as subqueries, joins, aggregations, etc.; SQL, or Structured Query Language, is a standard language for manipulating and querying data in relational databases, but it does not have procedural features.Reference:CompTIA DataSys+ Course Outline, Domain 1.0 Database Fundamentals, Objective 1.2 Given a scenario, execute database tasks using scripting and programming languages. The two options that have data manipulation and procedural scripting power are PL/SQL and T-SQL. PL/SQL, or Procedural Language/Structured Query Language, is an extension of SQL that adds procedural features to SQL for Oracle databases. PL/SQL allows users to create and execute stored procedures, functions, triggers, packages, etc., using variables, loops, conditions, exceptions, etc., in addition to SQL commands. PL/SQL helps improve the performance, functionality, modularity, and security of SQL queries and applications. T-SQL, or Transact-SQL, is an extension of SQL that adds procedural features to SQL for Microsoft SQL Server databases. T-SQL allows users to create and execute stored procedures, functions, triggers, etc., using variables, loops, conditions, exceptions, etc., in addition to SQL commands. T-SQL helps improve the performance, functionality, modularity, and security of SQL queries and applications. The other options are either not related or not having both data manipulation and procedural scripting power. For example, PQL, or Power Query Language, is a data analysis and transformation language for Microsoft Power BI and Excel; Advanced SQL is a term that refers to the advanced features or techniques of SQL, such as subqueries, joins, aggregations, etc.; SQL, or Structured Query Language, is a standard language for manipulating and querying data in relational databases, but it does not have procedural features.
Reference:
CompTIA DataSys+ Course Outline, Domain 1.0 Database Fundamentals, Objective 1.2 Given a scenario, execute database tasks using scripting and programming languages.
Question 5
Over the weekend, a company's transaction database was moved to an upgraded server. All validations performed after the migration indicated that the database was functioning as expected. However, on Monday morning, multiple users reported that the corporate reporting application was not working.
Which of the following are the most likely causes? (Choose two.)
- The access permissions for the service account used by the reporting application were not changed.
- The new database server has its own reporting system, so the old one is not needed.
- The reporting jobs that could not process during the database migration have locked the application.
- The reporting application's mapping to the database location was not updated.
- The database server is not permitted to fulfill requests from a reporting application.
- The reporting application cannot keep up with the new, faster response from the database.
Correct answer: AD
Explanation:
The most likely causes of the reporting application not working are that the access permissions for the service account used by the reporting application were not changed, and that the reporting application's mapping to the database location was not updated. These two factors could prevent the reporting application from accessing the new database server. The other options are either irrelevant or unlikely to cause the problem.Reference:CompTIA DataSys+ Course Outline, Domain 3.0 Database Management and Maintenance, Objective 3.2 Given a scenario, troubleshoot common database issues. The most likely causes of the reporting application not working are that the access permissions for the service account used by the reporting application were not changed, and that the reporting application's mapping to the database location was not updated. These two factors could prevent the reporting application from accessing the new database server. The other options are either irrelevant or unlikely to cause the problem.
Reference:
CompTIA DataSys+ Course Outline, Domain 3.0 Database Management and Maintenance, Objective 3.2 Given a scenario, troubleshoot common database issues.
Question 6
Refer to exhibit.
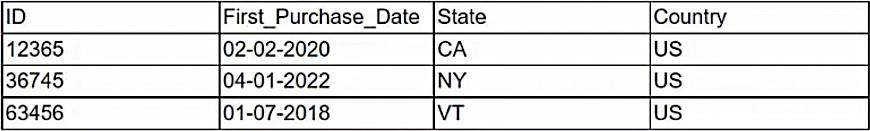
Given the following customer table:
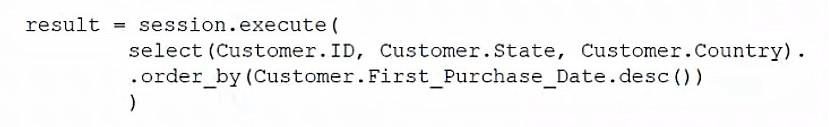
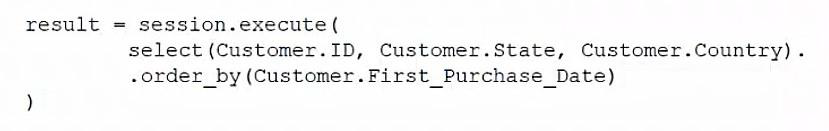
Which of the following ORM snippets would return the ID, state, and country of all customers with the newest customers appearing first?
Correct answer: C
Explanation:
The ORM snippet that would return the ID, state, and country of all customers with the newest customers appearing first is option C. This snippet uses theselectmethod to specify the columns to be returned, theordermethod to sort the results by ID in descending order, and theallmethod to fetch all the records. The other options either have syntax errors, use incorrect methods, or do not sort the results correctly.Reference:CompTIA DataSys+ Course Outline, Domain 1.0 Database Fundamentals, Objective 1.2 Given a scenario, execute database tasks using scripting and programming languages. The ORM snippet that would return the ID, state, and country of all customers with the newest customers appearing first is option C. This snippet uses theselectmethod to specify the columns to be returned, theordermethod to sort the results by ID in descending order, and theallmethod to fetch all the records. The other options either have syntax errors, use incorrect methods, or do not sort the results correctly.
Reference:
CompTIA DataSys+ Course Outline, Domain 1.0 Database Fundamentals, Objective 1.2 Given a scenario, execute database tasks using scripting and programming languages.
Question 7
A DBA is reviewing the following logs to determine the current data backup plan for a primary data server:
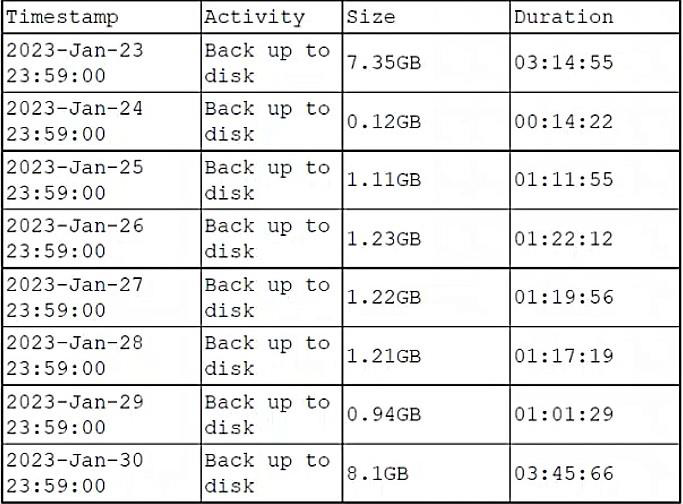
Which of the following best describes this backup plan?
- Monthly full, daily differential
- Daily differential
- Daily full
- Weekly full, daily incremental
Correct answer: D
Explanation:
The backup plan that best describes the logs is weekly full, daily incremental. This means that a full backup of the entire database is performed once a week, and then only the changes made since the last backup are backed up every day. This can be inferred from the logs by looking at the size and duration of the backups. The full backups are larger and take longer than the incremental backups, and they occur every seven days. The other backup plans do not match the pattern of the logs.Reference:CompTIA DataSys+ Course Outline, Domain 5.0 Business Continuity, Objective 5.2 Given a scenario, implement backup and restoration of database management systems. The backup plan that best describes the logs is weekly full, daily incremental. This means that a full backup of the entire database is performed once a week, and then only the changes made since the last backup are backed up every day. This can be inferred from the logs by looking at the size and duration of the backups. The full backups are larger and take longer than the incremental backups, and they occur every seven days. The other backup plans do not match the pattern of the logs.
Reference:
CompTIA DataSys+ Course Outline, Domain 5.0 Business Continuity, Objective 5.2 Given a scenario, implement backup and restoration of database management systems.
Question 8
A database administrator needs to ensure that a newly installed corporate business intelligence application can access the company's transactional data. Which of the following tasks should the administrator perform first?
- Create a new service account exclusively for the business intelligence application.
- Build a separate data warehouse customized to the business intelligence application's specifications.
- Set up a nightly FTP data transfer from the database server to the business intelligence application server.
- Send the business intelligence administrator the approved TNS names file to configure the data mapping.
- Open a new port on the database server exclusively for the business intelligence application.
Correct answer: A
Explanation:
The first task that the administrator should perform is to create a new service account exclusively for the business intelligence application. This will ensure that the application has the appropriate permissions and credentials to access the company's transactional data. The other options are either unnecessary, inefficient, or insecure. For example, building a separate data warehouse would require additional resources and time, setting up a nightly FTP data transfer would expose the data to potential breaches, sending the TNS names file would not guarantee that the application can connect to the database, and opening a new port on the database server would create a vulnerability for attackers.Reference:CompTIA DataSys+ Course Outline, Domain 2.0 Database Deployment, Objective 2.1 Given a scenario, install and configure database software and tools. The first task that the administrator should perform is to create a new service account exclusively for the business intelligence application. This will ensure that the application has the appropriate permissions and credentials to access the company's transactional data. The other options are either unnecessary, inefficient, or insecure. For example, building a separate data warehouse would require additional resources and time, setting up a nightly FTP data transfer would expose the data to potential breaches, sending the TNS names file would not guarantee that the application can connect to the database, and opening a new port on the database server would create a vulnerability for attackers.
Reference:
CompTIA DataSys+ Course Outline, Domain 2.0 Database Deployment, Objective 2.1 Given a scenario, install and configure database software and tools.
Question 9
Which of the following scripts would set the database recovery model for sys.database?
Correct answer: A
Explanation:
The script that would set the database recovery model for sys.database is option A. This script uses theALTER DATABASEstatement to modify the recovery model of the sys.database to full with no wait. The other options either have syntax errors, use incorrect keywords, or do not specify the recovery model correctly.Reference:CompTIA DataSys+ Course Outline, Domain 3.0 Database Management and Maintenance, Objective 3.1 Given a scenario, perform common database maintenance tasks. The script that would set the database recovery model for sys.database is option A. This script uses theALTER DATABASEstatement to modify the recovery model of the sys.database to full with no wait. The other options either have syntax errors, use incorrect keywords, or do not specify the recovery model correctly.
Reference:
CompTIA DataSys+ Course Outline, Domain 3.0 Database Management and Maintenance, Objective 3.1 Given a scenario, perform common database maintenance tasks.
Question 10
A database administrator is conducting a stress test and providing feedback to a team that is developing an application that uses the Entity Framework. Which of the following explains the approach the administrator should use when conducting the stress test?
- Capture business logic, check the performance of codes, and report findings.
- Check the clustered and non-clustered indexes, and report findings.
- Review application tables and columns, and report findings.
- Write queries directly into the database and report findings.
Correct answer: A
Explanation:
The approach that the administrator should use when conducting the stress test is to capture business logic, check the performance of codes, and report findings. This will help the administrator to evaluate how well the application handles high volumes of data and transactions, identify any bottlenecks or errors in the code, and provide feedback to the development team on how to improve the application's efficiency and reliability. The other options are either too narrow or too broad in scope, and do not address the specific needs of an application that uses the Entity Framework.Reference:CompTIA DataSys+ Course Outline, Domain 4.0 Data and Database Security, Objective 4.3 Given a scenario, monitor database performance and security. The approach that the administrator should use when conducting the stress test is to capture business logic, check the performance of codes, and report findings. This will help the administrator to evaluate how well the application handles high volumes of data and transactions, identify any bottlenecks or errors in the code, and provide feedback to the development team on how to improve the application's efficiency and reliability. The other options are either too narrow or too broad in scope, and do not address the specific needs of an application that uses the Entity Framework.
Reference:
CompTIA DataSys+ Course Outline, Domain 4.0 Data and Database Security, Objective 4.3 Given a scenario, monitor database performance and security.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!